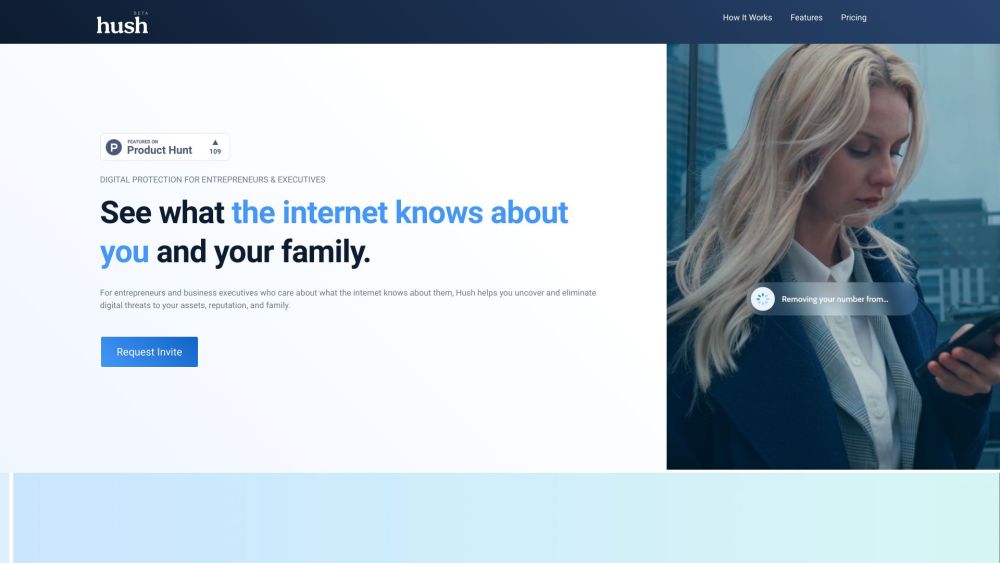
Hush Privacy AI
Hush offers advanced threat detection to safeguard companies against cleverly designed social engineering attacks.
Alternative Tools
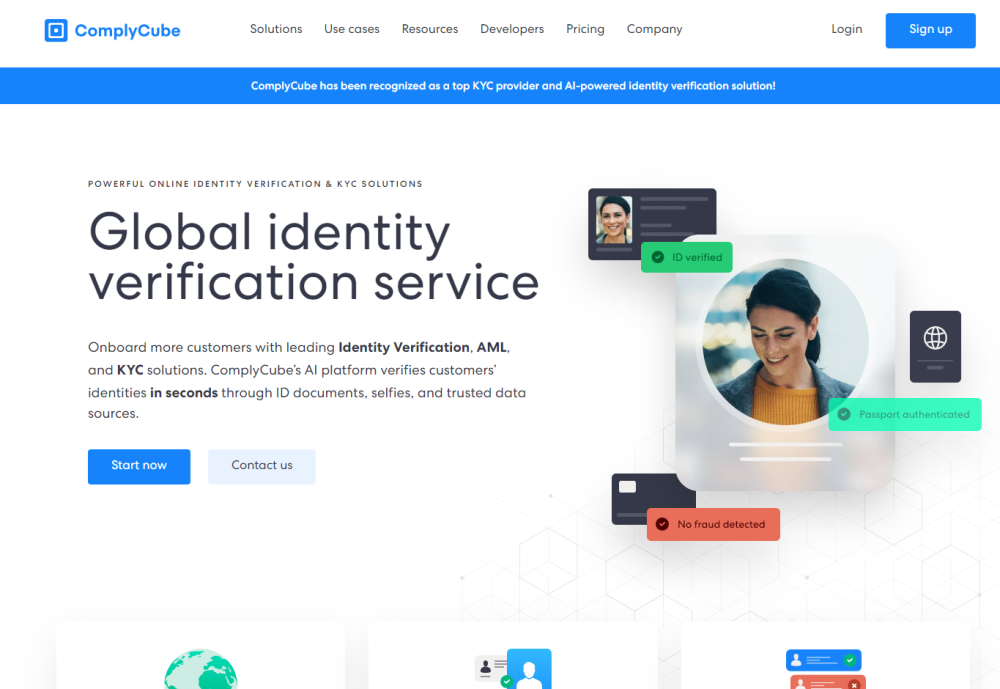
ComplyCube
ComplyCube is a leading software as a service platform providing swift and precise customer identity verification.
Text&Writing
Code&IT
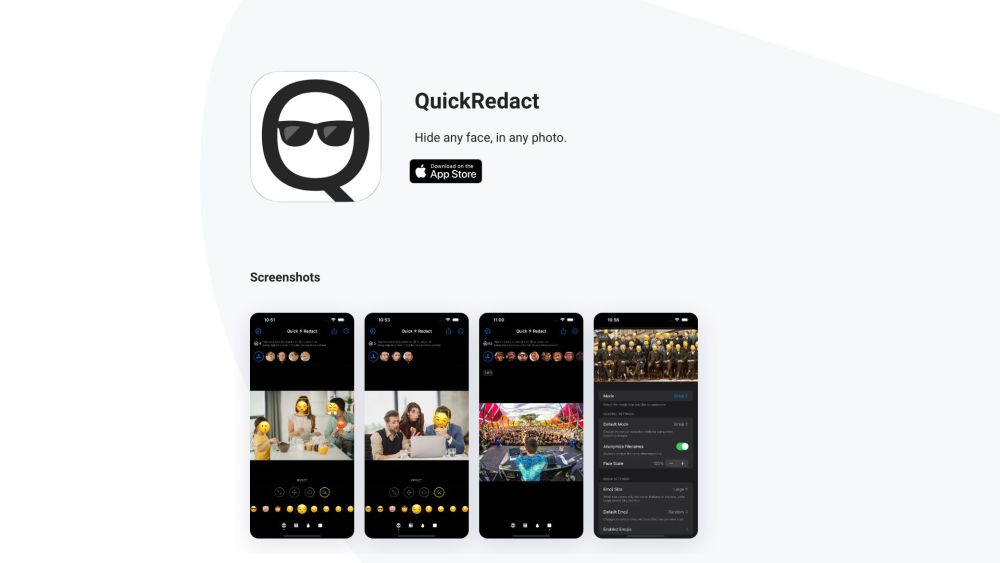
QuickRedact
Cover faces in images using QuickRedact, a sophisticated face identification system.
Text&Writing
Image
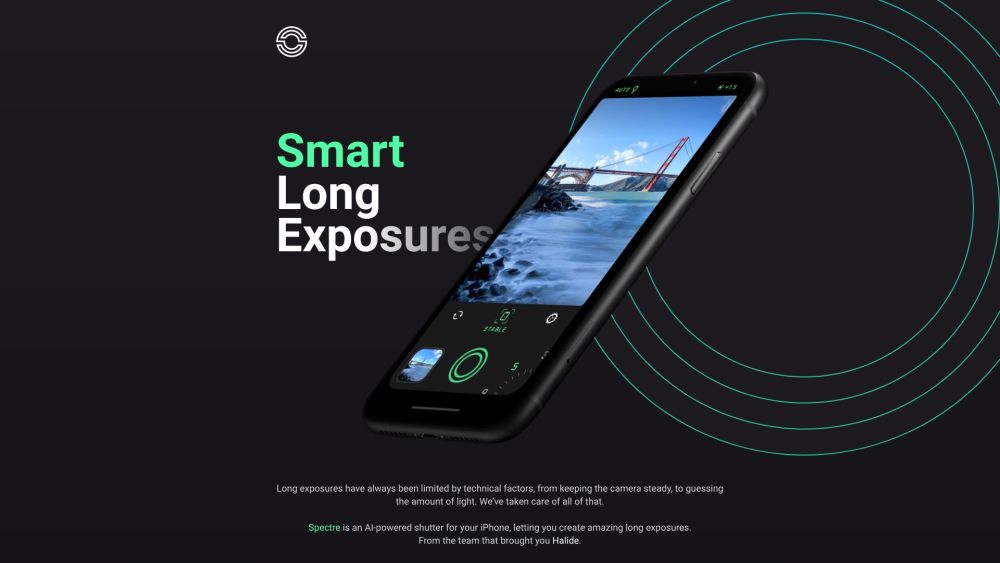
Spectre
A smartphone app that uses Artificial Intelligence for taking long exposure photographs.
Text&Writing
Image